Technical Specifications, Screen Shots, Interview With Chief Developer
Technical Specifications
If You Store Files In The Cloud,
Encrypt Them With KetuFile PRO
Specifications Common To All Models Of KetuFile
- Designed For Windows(tm) OSs: 98, NT 4.0 SP6a, 2000, XP, Win7.
- KetuFile may run on certain later versions of Win95 that have long file name support.
- KetuFile was not written to run on the Mac(tm) operating system.
Nevertheless it may be of interest to mention that, some users have
Virtual PC running Windows on their Mac and report that KetuFile runs
without problem.
- NOTE: Download and install/run DEMO program before purchasing license.
- Uses standard GUI interface.
- Allows specifying numerous different Keys for encryption/decryption.
- Allows saving Keys on User's hard disk with a Nick Name.
- Saves Keys on User's hard disk as encrypted.
- Prepends a Header to encrypted files that include the Key Nick Name
- Excellent Inbound Email integration. Launches KetuFile from within Email client.
- Excellent Outbound Email integration. Launches Email client from within KetuFile.
Specification Differences For KetuFile Models
Specification DEMO Standard Pro
------------------------ ------------ ------------ -----------
File Size for encryption 100 kilobytes 10 megabytes 2 gigabytes
Key Length 8 bits 256 bits 512 bits
NOTE: See the 'Summary Description' for more detail on the number of
possible keys with the KetuFile 256 Bit keys and the KetuFile 512 Bit keys.
Allowable Decryption
Any model of KetuFile, including the free Demo model, can decrypt any KetuFile encrypted file of any Key length.
Screen Shots


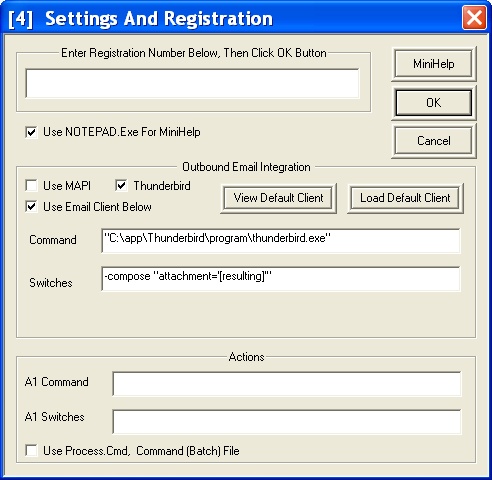
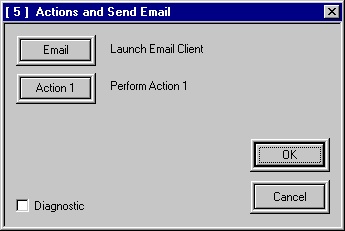
Interview With Chief Developer
Table Of Contents
Interview With Chief Software Developer, Robert Palma
What is KetuFile?
Why would anyone want or need to use it?
When would a user want to use this?
Just how easy is it to use?
That brings up a question, what is a Key?
So a user could use their name or phone number or something like that, for a Key?
Okay, I'll bite, what's a Dictionary attack?
When a file is encrypted it is changed into an encrypted state. Is this correct?
So it is this "encrypted version" that a user might send out attached to an email?
Will KetuFile work with all versions of the Windows(tm) operating system?
Does the Demo version actually encrypt and decrypt?
Once a user determines that the Demo works on his/her machine, how do they get the Standard or Pro version?
It's as simple as that? No new software to install?
When the Demo version is initially installed, is it easy or complicated to do?
If I want to send an encrypted attachment to someone, then we both need to have KetuFile, yes?
How do I send the Key to them?
Let's say I receive an email from someone with an attached spreadsheet. What do I have to do to decrypt it?
There are other encryption programs out there, why should users be interested in KetuFile?
I guess in the computer world, we are always upgrading for faster performance and new features, so moving to KetuFile is like this. Yes?
I can guess what Backdoors are, but what is Key Recovery?
So if I'm using the XYZ encryption program, and it has Key Recovery built in, then that means that someone, somewhere can decrypt my message/file, without me giving them the Key. Yes?
How long would it take them to do this?
So I'm in trouble if the person or group that has this Key Recovery information is someone who is a competitor, etc?
If someone has Key Recovery for encrypted messages/files that I generate using XYZ, do they also have the ability to perform Key Recovery on other peoples encrypted messages/files that were encrypted with XYZ?
So its a global problem?
I hope that whoever has this Key Recovery ability is my friend.
Then anyone in the world could perform Key Recovery and decrypt anyone's messages/files, if they had been encrypted with XYZ?
So if a person or organization uses KetuFile they will be safe?
One more techie question. KetuFile allows a maximum of 256 bits (Standard) or 512 bits (Pro). Just how big of a number is that?
You've provided us with a great deal of information on the area of encryption. How long have you been an expert in this area?
I can't resist this question. Are you a rocket scientist?
What do you recommend that users do next?
What is KetuFile?
KetuFile is an easy-to-use Windows(tm) application that allows strong encryption of any type of PC file, including text, word processor, spreadsheet, graphics, binaries, executables.
Why would anyone want or need to use it?
Let me respond by posing some questions to you and your readers. What would happen if your company's patents, engineering documents, financial records, customer lists, employee files, contracts, briefs, and other private, privileged information got into the wrong hands? What if the media was able to snoop into your communications? What would happen if your banking and credit card information were compromised? Could your competitors use any of the aforementioned to gain an unfair advantage? Ketufile allows these important documents and information to be encrypted (scrambled, so to speak) so that if an unauthorized person obtains or intercepts them, they will be, literally, gibberish.
On the other hand, when an authorized person receives this encrypted file, they can use KetuFile, and the Key to turn it back into its original state.
When would a user want to use this?
Perhaps the greatest exposure to compromise is when a user attaches any type of PC file, (including text, word processor, spreadsheet, graphics, binaries, and executables) to an outgoing email. People do this all the time with very sensitive data. There are many, many ways that such email and their attachments can be intercepted. If the attachments are encrypted first, then when they are intercepted, they are useless gibberish. Keep in mind that many industry experts say that email is the biggest application/use on the entire Internet.
Files can also be encrypted before they are stored or archived. KetuFile Pro will encrypt up to a 2 gigabyte file.
Just how easy is it to use?
It is a full Windows(tm) Graphical User Interface (GUI) application program. It has all the point-and-click, mouse-driven features that Windows users are used to. A user simply clicks on a desktop shortcut or uses the Start button and runs the KetuFile program. They will be presented with a familiar looking Dialog box. Using the built-in features of KetuFile, the user can browse through his/her hard disk files to find the one they want to encrypt. The user must also specify a Key. He/she may type in a Key or select one that has been saved from a previous session with KetuFile. Just one or two more clicks and the encryption process begins.
That brings up a question, what is a Key?
In the KetuFile program, the Key is a series of numbers and letters that are used to encrypt a message/file. When the party who receives an encrypted message/file, wishes to decrypt to get back the original, this same Key will be used.
So a user could use their name or phone number or something like that, for a Key?
They could but that would be a really bad idea. It would result in an encrypted file that was not really secure. A major element in the robustness of KetuFile is the randomness of the Key that the user selects. This is true for any system of encryption, not just KetuFile. Any use of personal data (phone numbers, names, addresses, or words or terms from any language) will leave the encrypted file open to a Dictionary attack.
Okay, I'll bite, what's a Dictionary attack?
Decryption is the reverse of encryption. Anyone who wishes to try to decrypt (unscramble) an encrypted file or message, and is not authorized to do so, is doing what is called "cracking". You can think of cracking as unauthorized decryption. This is much like someone physically cracking into a safe at, say, a bank. Since it is common, unfortunately, for people to use words or phrases for Keys from an existing language (English, French, whatever), the person who is cracking can use existing computer-based dictionaries of various languages and try to decrypt (crack) the message or file. This (a Dictionary attack) can be literally billions of times faster than simply trying every possible Key.
When a file is encrypted it is changed into an encrypted state. Is this correct?
No. Another file is created, that is an encrypted version of the original file. The original file is still there in its same location on the computer hard disk, untouched. KetuFile simply reads the original file and creates an encrypted version of it.
So it is this "encrypted version" that a user might send out attached to an email?
Yes.
Will KetuFile work with all versions of the Windows(tm) operating system?
It will work with almost all of them. There are many different Windows operating systems, different versions of each of them, not to mention many service packs, patches, etc. We have tested KetuFile with Win 98, NT, Win2K, XP, Win7, and found no problems. We have run KetuFile successfully on Win95 systems of the later versions that have long file name support. One of our customers runs KetuFile on the MAC, using an emulation program that let's the MAC run Windows programs. We don't support this, though.
Anyone can download the Demo program, install it on his/her machine and operate it, prior to purchasing a license for it. We encourage this.
Does the Demo version actually encrypt and decrypt?
Yes. It restricts the Key length to 8 bits and the file-to-be-encrypted size to 100 kilobytes. Other than that it operates fully as the Standard and Pro versions. If the Demo runs on a particular machine, then the Standard and Pro will run also.
Once a user determines that the Demo works on his/her machine, how do they get the Standard or Pro version?
They purchase a license. This is delivered to them as a Registration Number that they type into their Demo version. This Registration Number "wakes up" the Standard or Pro features, namely longer Key sizes and longer file-to-be-encrypted sizes.
It's as simple as that? No new software to install?
Yes it's as simple as that. The user simply types in the Registration Number.
When the Demo version is initially installed, is it easy or complicated to do?
We have worked hard to make this easy! The user downloads a single file from our web site. It is called Setup.EXE. The user places this file in a folder by itself, then double clicks on it. The KetuFile installer runs in a simple interactive way and quickly installs the program, registers it with the operating system, and then the user is ready to go. In most Windows operating systems, the user must have Administrator privileges to install new software.
If I want to send an encrypted attachment to someone, then we both need to have KetuFile, yes?
Yes.
How do I send the Key to them?
You need to convey the Key in a secure manner. This could be a fax, telephone call, or some personal contact. It would NOT be advisable to send a Key by email. This would likely defeat the whole security approach.
Let's say I receive an email from someone with an attached spreadsheet. What do I have to do to decrypt it?
The short answer is that you will simply click (or double click) on the attached file (within your email program) and the operating system (Win NT, for example) will run KetuFile and send KetuFile the name and location of the file-to-be-decrypted. You then click within the KetuFile program to start the decryption. It is very quick.
Now here's the long answer.
First of all, let's talk about Keys. A Key is a random sequence of letters and numbers. Here is an example:
kW4o8GMvae3diHeQ4k9lApXU6n1bDeFs
The above is a 32 character Key. Since there are 8 bits per character, this represents a 256 bit Key.
Keys can have a Nickname, just as people do. Let's give a Nickname to the above Key. If a person named Joe will using this Key to send encrypted email attachments to a person named Mary, they could use a Nickname of: joemary
So, Joe runs KetuFile, manually types in the above 32 character Key, then tells KetuFile to save the Key with a Nickname, joemary.
Then Mary runs KetuFile on her machine, manually types in the above 32 character Key, then tells KetuFile to save the Key with a Nickname, joemary. They only have to do this one time.
Now Joe sends a confidential spreadsheet to Mary. He uses the joemary Key when he encrypts it. When Mary receives the email, she clicks on the attached file (the encrypted version of Joe's spreadsheet). Mary's operating system runs KetuFile and tells KetuFile where to find this encrypted file. KetuFile, in turn loads the encrypted file, loads the joemary Key from Mary's hard disk and tells Mary (through a message that pops on screen) that its ready to decrypt. She just "click, clicks" and KetuFile decrypts that file, bringing it back to its original state.
There are other encryption programs out there, why should users be interested in KetuFile?
There are a lot of reasons. KetuFile is based upon Advanced Encryption Standard (AES). AES is the latest US standard for encryption. It is the result (the winner) of a global competition. I think most people will immediately form a favorable opinion of KetuFile based upon this fact alone.
I guess in the computer world, we are always upgrading for faster performance and new features, so moving to KetuFile is like this. Yes?
Mmmm, it is much more than that. When you upgrade your computer memory, speed, etc., you hopefully get better computational and data handling efficiency, but it is NOT that your old system stops working.
With encryption, the need to "move up" is much more urgent, because your old encryption approach may "stop working".
In the area of encryption, there is a phenomenon known as Evolution Of Attacks. This means, as time goes by, analysts learn more about a particular encryption system, and therefore can crack it in shorter and shorter times. Many cryptographers have written that any encryption approach will, in time, be efficiently cracked. Therefore, what I mean when I say that an encryption approach will "stop working" is that it has been around long enough that it can be cracked in a short period of time and you don't have good protection. Keep in mind that new approaches to cracking are often published publicly.
So not only does KetuFile use the latest global standard for encryption (AES) and thereby not have a decade of people learning how to crack it efficiently, but KetuFile does not have any Backdoors or Key Recovery features. If you read the literature that is publicly available you might be surprised to see that certain popular encryption approaches/programs have Key Recovery built in.
I can guess what Backdoors are, but what is Key Recovery?
Let's talk about both of them. 'Back Door' is a widely used, and widely defined term-of-art. In the case of KetuFile, it would refer to the existence of a decryption process that can be applied to a given encrypted message/file, that does not need the original encrypting Key. If an encryption product has such a back door it is, in essence, crippled. There are no 'back doors' whatsoever in KetuFile.
'Key Recovery' means that there is a way that the user's Key can be deduced from either the encrypted message/file , i.e. the key is secretly buried in the encrypted message/file, or some other approach allows a third party to get or generate any users key. If an encryption product has such a Key Recovery feature, it is in essence, crippled. There are no 'Key Recovery' features whatsoever in KetuFile.
So if I'm using the XYZ encryption program, and it has Key Recovery built in, then that means that someone, somewhere can decrypt my message/file, without me giving them the Key. Yes?
Yes.
How long would it take them to do this?
I can't really say, but I would guess "in the blink of an eye".
So I'm in trouble if the person or group that has this Key Recovery information is someone who is a competitor, etc?
You can answer that question.
If someone has Key Recovery for encrypted messages/files that I generate using XYZ, do they also have the ability to perform Key Recovery on other peoples encrypted messages/files that were encrypted with XYZ?
Yes.
So its a global problem?
Yes.
I hope that whoever has this Key Recovery ability is my friend.
The situation is far more serious than that. Using your example, if Key Recovery exists for the XYZ encryption program, then it is possible that some other person or organization could discover the Key Recovery process by extensive analysis on a particular encrypted message/file. Depending on whom that other person or organization is and why they performed this analysis and discovery, the results of their work could be made public.
Then anyone in the world could perform Key Recovery and decrypt anyone's messages/files, if they had been encrypted with XYZ?
It is scary.
So if a person or organization uses KetuFile they will be safe?
There are really quite a number of tasks and areas that must be looked into to protect confidential information. File encryption that is truly robust (KetuFile), is just one of them. Our web site touches on numerous other areas that must considered.
One more techie question. KetuFile allows a maximum of 256 bits (Standard) or 512 bits (Pro). Just how big of a number is that?
The approximate number of possible keys for a 256 bit KetuFile key ( 2^252 ):
a Trillion x Trillion x Trillion x Trillion x Trillion x Trillion
The approximate number of possible keys for a 512 bit KetuFile key ( 2^508 ):
a Trillion x Trillion x Trillion x Trillion x Trillion x Trillion x Trillion x Trillion x Trillion x Trillion x Trillion x Trillion
A Trillion is defined (in the U.S.) as: 1,000,000,000,000
You've provided us with a great deal of information on the area of encryption. How long have you been an expert in this area?
I actually do NOT consider myself an expert in encryption or cryptography. An expert in this area will have a degree in mathematics, preferably an advanced degree. In addition, he/she will have a Curriculum Vitae that has a long list of publications in referred journals on the subject of cryptography/encryption.
I am a scientist, a research and development engineer by training. I spent more than 2 decades designing and building satellites and rockets for the US military where we used encryption in many, many places. I not only performed hardware/software designs for spacecraft, but served as Chief Engineer of satellite development. As such I have the ability to read the scientific literature and to choose a truly strong approach to encryption (AES) and create an application program (KetuFile) to provide it to users.
I can't resist this question. Are you a rocket scientist?
I have been called that quite a bit.
What do you recommend that users do next?
Read the KetuFile web site.
http://www.ketufile.com
Download and install the Demo program. An IT Manager at a firm/organization could literally install it on every ones desktop in the Demo mode and let people try it out. Once they decide to use it, they need to purchase licenses (Registration Numbers) for each machine (PC).
Also, there are companies that specialize in security and they can be contracted-with to assess the needs of a particular organization. I offer the following warning: when you ask them for an assessment of whether the "this" or "that" system of encryption is strong and robust, make sure they have proper cryptography credentials. Again, an expert in this area will have a degree in mathematics, preferably an advanced degree. In addition, he/she will have a Curriculum Vitae that has a long list of publications in referred journals on the subject of cryptography/encryption.
Press 'Back' On Your Browser To Return To Previous Page
|